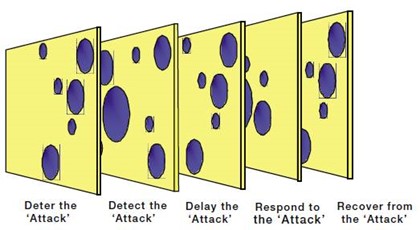
The Vulnerability Assessment, commonly referred to as Defence in Depth, is the process of rating the site’s vulnerability to the potential crimes or incidents identified in the threat assessment.
By this stage, several site audits should have been conducted reviewing CCTV, locks, alarms and other measures that can prevent opportunities for offenders to commit a crime. This analysis should have been conducted using the vulnerability tables provided in this section.
The framework has been developed to identify practices and infrastructure that, if put in place and used appropriately, can reduce the opportunities for crime.
The model is known as the R2D3 model. This model involves an analysis of the site and an assessment of the school’s infrastructure and practices that can contribute to reducing crime through:
- Deterring the offender by staff actively engaging with customers, such as stopping people from entering the site without visitor tags
- Detecting an offender, for example, through means such as CCTV
- Delaying the offender by locking doors and windows
- Responding to an incident as a result of a fire or breach of alarm
- Recovery procedures after an attack, such as counselling for a victim of a crime
Defence in Depth – Swiss Cheese Model
Crucial to this process is identifying the critical ingredients for crime to occur assessing what measures are in place and how effective they are. By removing the key ingredients and reducing the gaps that provide the opportunity to offend, crime can be prevented. Such a criterion is designed to prevent crimes that would have financial, physical and reputational consequences for staff, contractors and site property.
The vulnerability assessment is a series of questions that have been compiled to review a site systematically. If additional issues or gaps are identified, they need to be identified and the project manager informed so they can be added for future assessments. The gaps and meaningful opportunities for offending should have been identified through numerous site audits during the day and night, reviewing policy and procedures and extensive consultations with staff, contractors and students.
In the example of an SRA conducted on a site years ago, the vulnerability assessment identified several gaps, which will later inform the recommendations. Some of these gaps include:
- Lockdown drills not conducted
- Cleaning staff not securing rooms after cleaning, providing opportunities for potential offenders to enter buildings
- Access through the dining room door late at night provides access to the reception and tower steps.
- Bedroom doors are unlocked throughout the day, and personal items are not secured while contractors work.
- The first aid door was not secure late at night, providing access to the dormitory.
- Caretaker conducting banking duties at the same time every day in uniform and without risk assessment or training,
- Faulty locks on year 12 common-room door and others provide access to the Hall Classrooms,
- Windows not secured in Main Hall Classrooms provides easy access to all classrooms,
- Continuous open plan (no doors locked) design throughout Main Building Classrooms provides for easy access to all parts of the building.
- Landscaping is overgrown, providing concealment opportunities.
The next step in the security assessment process is to identify the specific opportunities for crime to occur at the site.
The SRMO achieves this by allocating a vulnerability rating to each offence, using a different set of qualitative criteria. The following framework has been adopted from the Security Risk Management Handbook to identify the site’s vulnerability to the nominated crime types.
Vulnerability assessment
The next step in the process is to undertake the vulnerability assessment. The first step in the vulnerability analysis considers how each of the threats from the threat assessment can be realised against each of the critical assets from the scope of works (from the criticality assessment). This involves determining:
- Potential means by which a successful ‘attack’ against the property or people could be carried out (e.g. how could a thief gain access to petty cash during lunchtime?),
- The effectiveness of each layer of security in preventing an incident or event occurring against people or property. Now refer to the CHD Partners Vulnerability Checklist.
When rating the site’s vulnerability, the vulnerability assessment requires a thorough analysis of the site infrastructure and practice, identified during site audits, consultation and procedure reviews. The following table provides the vulnerability ratings from the Security Risk Management Handbook (HB167:2006), which will be used throughout the vulnerability assessment.
Table 1: Vulnerability assessment matrix: HB 167:2006 Security Risk Management Handbook
| Level | Assessment criteria |
| Extreme | Controls are non-existent. Critical and urgent improvements needed have been identified.
It is almost certain that controls will be breached or will fail. There is recent evidence of widespread control failures. There are no contingencies in place, and severe disruptions to the business are likely. |
| High | Controls are largely ineffective. Significant areas for improvement have been identified.
It is likely that the controls will be breached or will fail. |
| Moderate | The majority of controls are functioning, but a number of areas for improvement are identified.
There is a moderate probability of the controls being breached. There is recent evidence of a small number of controls being breached. |
| Minor | Controls are effective, but small improvements could be made.
There is a low probability of the controls being breached in the future. There are no recent examples of controls being breached. The adequacy of the controls is assessed on a regular (minimum annual) basis. |
| Low | Controls are optimal and are sustainable.
There is an extremely low probability of the controls being breached in the future. There are no previous incidents of the controls being breached. The adequacy of the controls is assessed regularly and frequently. |
Now, identify security deficiencies, complete the vulnerability table, and then rate them using the criteria above.
For example, the vulnerability rating of an assault occurring against a student or staff member by an external source can be determined using the qualitative framework provided above. In this example, a rating of ‘possible’ was selected after the consultant considered the number of security breaches.